EncroChat: What You Need to Know
Article by Harewood Law.
EncroChat - What Happened?
On the 13th June 2020, EncroChat, one of the world’s largest encrypted communication providers, sent a message to its 60,000 subscribers, 10,000 of whom were in the UK, informing them that their protected systems had been compromised. This coincided with the National Crime Agency (NCA) launching “Operation ‘Venetic”, an operation that consisted of multiple raids across the country and resulted in 746 arrests, £54 million in cash being seized, as well as luxury watches, 77 firearms, grenades, an AK-47 rifle, sub-machine guns and 2 tonnes of drugs. Months of monitoring messages culminated in the NCA taking action.
EncroChat guaranteed users anonymity by automatically deleting messages remotely and completely wiping data if anyone tried to hack the device or access messages. EncroChat realised that its service had been infiltrated in the middle of June, but the exact date of the interception may have been months earlier. This was a coordinated effort across Europe. The actual method used for the hack/interception is unclear at this stage.
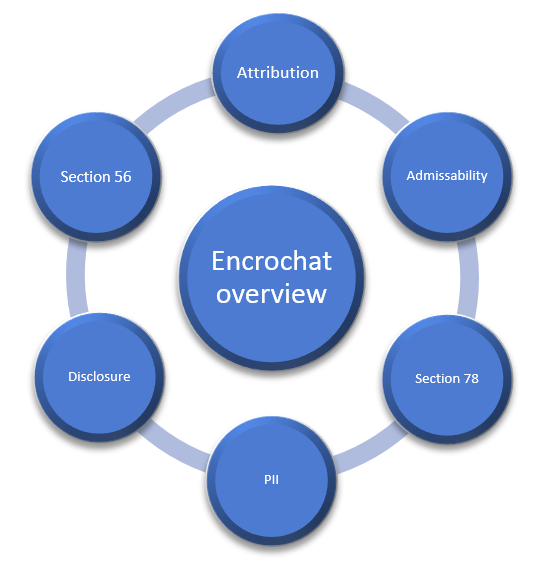
Many of the suspects arrested were released under investigation or released on police bail after the initial police interviews. Others are still to be arrested. However, there are cases now in court. Importantly, as these cases move through the various Crown Courts, we should get clarity on many aspects. Disclosure in court by the Crown Prosecution Service should identify the method used by the NCA to infiltrate the EncroChat platform, when the information was first obtained, what information was obtained and what information will be used in court. This will result in legal applications that will inevitably require a judicial ruling. There may be applications to stay the proceedings (section 78 of PACE), admissibility arguments or PII applications. Much of the mystery around how the evidence was obtained and whether it can be used will be clarified.
Is Using EncroChat illegal?
Using EncroChat is not illegal. In some cases, however; the police may wish to speak to individuals about the contents of their messages.
Every case will be different; there is no generic guidance that can apply to every case. Below are the type of questions that will be considered in these cases:
Is the device or the messages attributable to you?
What is the context of the messages?
Are the messages incriminating, or can alternative interpretations apply?
Was the information obtained legally?
IPA law
Even if the information was illegally obtained, is it admissible in court?
Can the proceedings be “stayed” as an abuse of process?
Does section 78 of PACE apply?
Are proper disclosure procedures followed?
Can you be assured a fair trial?
Was special counsel used and the correct procedure followed?
PII - Public Interest Immunity concerns
Jurisdictional issues
The prejudicial effect of the association of the term “EncroChat” with “criminality”.
Breach of European Convention of Human Rights
As you can already see, certain legal issues are more relevant to some cases than others. It is hoped that by the end of August, there will be some clarity coming from the courts as the cases move through the system and evidence is served.
Relevant Cases
Below are a number of cases that have dealt with similar issues.
The Michael O’Loughlin case in the Irish News was a case involving EncroChat use. Offences included ‘Conspiracy to Commit Murder’, ‘Conspiracy to Possess Firearms’ and ‘Conspiracy to Rob’. An Officer to the Court stated, “The evidence against O’Laughlin has been obtained by lawfully authorised clearance that has enabled access to his encrypted mobile phone content”. This case will be dealing with many of the legal issues arising.
Virdee v NCA [2018] German police provided the NCA with recordings from an unrelated case that were used by the NCA to prosecute a bribery case.
R v Knaggs [2018] Dutch intercept evidence, questioned, s78 argued, disclosure issues, this case went to the Court of Appeal.
Court of Appeal R v Coulson and Others [2013] A case of voicemail interception (the infamous News of the World phone hacking scandal). This was an exception to the "successful transmission" rule. The case dealt with voicemails but discussed intercepted evidence.
R v Austin [2009] “It is well established that a failure by the crown to comply with its duty of disclosure will constitute a ground of appeal”.
R v H [2004] Dealt with PII material and special counsel issues.
R v Ward (1993) “None disclosure is a potent source of injustice and even with the benefit of hindsight, it will often be difficult to say whether or not an undisclosed item of evidence might have shifted the balance or opened up a new line of defence”.
R v Aujla [1997] Facilitating illegal entry into the UK. Questions were raised about the Interception of phone calls by the Dutch Authorities, Section 78 PACE 1984. In the circumstances of that case the evidence was allowed.
R v P [2002] A Europe-wide drugs case. The case reached the House of Lords. The use of an interception can amount to interference under Article 8, but in these circumstances, the evidence was allowed.
Court of Appeal [R v English & Read (2020)] encrypted phones were considered an “aggravating” feature.
Court of Appeal (R v English & Read [2020]) The use of encrypted phones allowed the operation to be described as “sophisticated”.
If you are concerned about being arrested for any offence involving the use of an EncroChat phone or any other encrypted device, please contact our specialist team on 0333 344 8377. Our leading team of solicitors, barristers and Queen’s’ Counsel will represent your interests.
Communication keeps evolving
Communication methods keep developing. Every year, technology gets smarter and security gets more technical. End-to-end encryption is now an industry standard.
If you listen to or read the news, it seems to suggest that EncroChat technology was used solely by criminals, but in reality, it may simply be another form of secure communication. This is an issue that needs to be addressed at trial. That is not to say that criminals have not used this particular technology for criminal reasons, but that the media suggesting that criminals are the only users. A clearer picture needs to emerge that distinguishes between criminal usage and ordinary usage of this secure technology.
The Buzz around the EncroChat Hack
The hacking of EncroChat in the context of previous legal or illegal hacks should come as no surprise, but the press coverage seems to suggest that it is the “Hack of the Century”. If it is proved that every user of the technology was using it for criminal endeavours, then it may well be, but things are far from clear at this stage. There seem to be thousands of users who have not been investigated at all at this stage.
Remember PGP
PGP was a previous technology that was compromised.
Before we ever heard of EncroChat, there was a similar technology, another encrypted platform, again not solely used for advancing criminal activities.
For those of you who don't know, PGP stands for "Pretty Good Privacy". It was first developed in 1991, when we didn't really know what encryption was. It was standardised into OpenPGP from 1997. Edward Snowden, the famous whistle-blower, used this technology. It was one of the dominant forms of end-to-end encryption for email since the 1990s. Since Snowden, open-source PGP became more popular with whistle-blowers, dissidents and human rights activists. But, in the now-famous 14 May 2018 incident, a serious flaw was found in the armoury of this system. The hack dubbed "Efail" tricked email clients into revealing encrypted messages. The entire set-up was compromised. PGP was also technically complicated to use. When security flaws appeared, the technology left its users vulnerable, and as a result, its popularity among users began to fall.
Prior to the 2018 "Efail" hack, a bigger blow to PGP had already come in 2016, when the technology was given press attention in the infamous case of Shilling and Defraine. This also coincided with a launch by the European police of an offensive against PGP providers. They arrested the head of Ennetcom (a leading PGP company) and its servers were seized. this led to a reduced demand for PGP, but there was now growing demand for secure communication. Technology was advancing fast and digital security was becoming paramount with the rise of a new breed of technologically advanced hackers.
The 2016 case of Harry Shilling and Michael Defraine involved importing firearms from Europe. The NCA monitored them and successfully decoded PGP encryption software used on their multiple Blackberries. Again, the NCA had managed to access a secure method of communication.
New Tech
The emergence of new technology resulted in 50 million downloads of encrypted messaging apps such as Telegram and Signal by 2016. Then, Apple's iPhone with its iMessage service, and of course WhatsApp, turned more than a billion people on to end-to-end encryption. This has arguably done the most to take encryption to the masses. The process is now seamless.
The Arrival of EncroChat Secure Encryption
In simple terms, end-to-end encryption means that data sent to a recipient is scrambled, meaning that the only people able to read the conversation are the sender and the recipient. EncroChat was based in the Netherlands, and its handsets were not available in standard mobile phone shops. Instead, they were advertised over the internet. The EncroChat website, which has since been removed, described its service as a "user friendly secure instant messaging client" with "guaranteed security", "using end to end encryption and servers that never store messages". Users' data or keys are used to decipher exchanges. The appeal is clear.
The modified handsets, which did not operate like conventional smartphones, could cost around £1500 for six months’ use. Some of the models used were BQ Aquaris X2, an Android phone made by a Spanish manufacturer.
EncroChat removed each phone’s’ GPS, camera and microphone and installed its own apps before selling them to users. Data on the devices could be deleted remotely if seized.
EncroChat could be used in a number of ways, either as a normal phone or by discreetly using the EncroChat functionality. By changing the combination of buttons you pressed, you had access to a normal Android Phone or the EncroChat facility.
Key features:
Encrypted emails (limited)
Encrypted calls (limited)
Encrypted messages
End-to-end security solutions
Difficult to connect Sim Card or Device to customer
Two operating systems: standard OS Android Or EncroChat OS
Improved Security
Camera, microphone, GPS and USB removed
Main function instant messaging
Kill pills could delete messages (remotely)
Messages that self destruct
Screen lock wipe using pin
Internal self checking for tampering
Appearance of an ordinary handset
Discretion guaranteed
Unhackable
Used by criminal groups to avoid detection
Used by celebrities and businessmen for security
Media Attention: EncroChat
The first time EncroChat technology was highlighted in a case:
In the now-infamous gangland killings of Paul Massey and John Kinsella, Mark Fellows and Steven Boyle were charged with murder. Although there was no decryption technology in 2018, their use of EncroChat phones was used against them at trial. This case provided some publicity for EncroChat technology. It also highlighted the fact that in the gangland underworld, the use of technology was changing and becoming more sophisticated.
Operation Solero involved Andrew Venna, described by a judge as the CEO of a crime group, and Mathew Cornwall, his trusted second in command, used EncroChat Phones to communicate with each other.
The Future of Secure Technology
With the advancement of smartphones, we are able to undertake almost all of our transactions, including banking and online purchasing, using our phones. Therefore, data and phone security has become more important than ever. Criminals obviously use encrypted phones for criminal activity, but to suggest that is the only use for them is misleading.
Even though EncroChat may now officially be closed, secure smartphones will continue to become more advanced. Data security is becoming increasingly important, particularly in the post-Covid-19 world, where demand for remote digital services and platforms is increasing exponentially. There are many examples of similar companies already in existence that will fill any void left by EncroChat.
Written by Harewood Law.
If you are concerned about being arrested for any offence involving the use of an EncroChat phone or any other encrypted device, please contact our specialist team at Harewood Law at 0333 344 8377.
Our leading team of solicitors, barristers and experts will be available for advice and assistance.